Image Credits: Just_Super / Getty Images
Image Credits: Just_Super / Getty Images
Days after it was knocked offline by a sweeping, years-in-the-making law enforcement operation, the notorious Russia-based LockBit ransomware group has returned to the dark web with a new leak site complete with a number of new victims.
In a verbose, borderline-rambling statement published Saturday, the remaining LockBit administrator blamed its own negligence for last week’s disruption. A global law enforcement effort launched an operation that hijacked the ransomware gang’s infrastructure by exploiting a vulnerability in LockBit’s public-facing websites, including the dark web leak site that the gang used to publish stolen data from victims.
“Operation Cronos,” as the feds dubbed it, also saw the takedown of 34 servers across Europe, the U.K., and the U.S., the seizure of more than 200 cryptocurrency wallets, and the arrests of two alleged LockBit members in Poland and Ukraine.
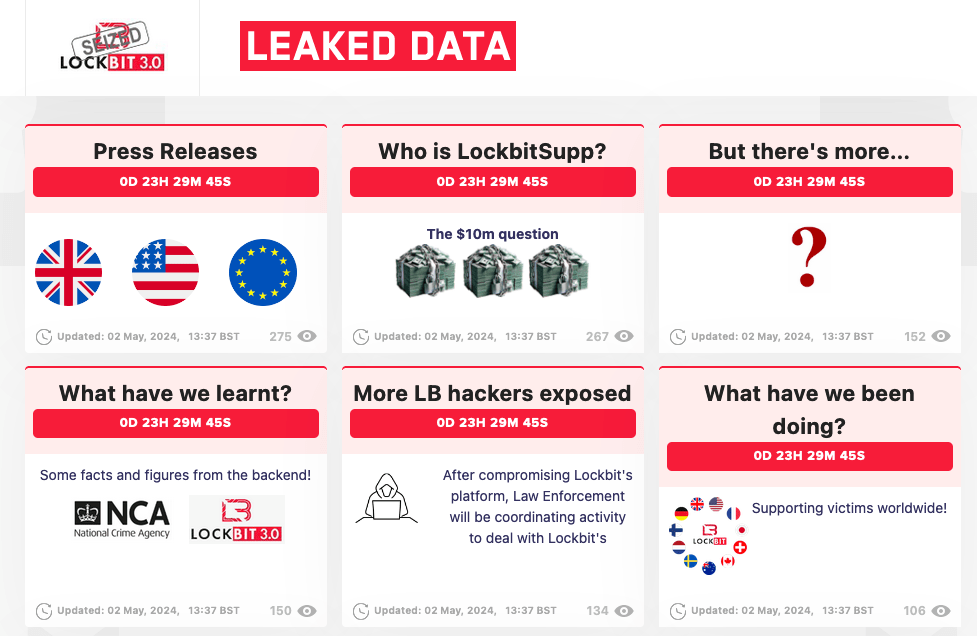
Just five days on, LockBit announced that its operations had resumed, claiming to have restored from backups unaffected by the government takedown. In its statement, LockBit’s administrator threatened to retaliate by saying it would target the government sector.
A spokesperson for the National Crime Agency, which led Operation Cronos, told TechCrunch on Monday following LockBit’s return that its takedown operation “successfully infiltrated and took control of LockBit’s systems, and was able to compromise their entire criminal operation.”
“Their systems have now been destroyed by the NCA, and it is our assessment that LockBit remains completely compromised,” the NCA said.
Law enforcement claiming overwhelming victory while the apparent LockBit ringleader remains at large, threatening retaliation, and targeting new victims puts the two at odds — for now. With more than a dozen new victims claimed since its brazen relaunch, LockBit’s demise might have been overstated.
As the cat-and-mouse game between the feds and the criminals rolls on, so does the fighting talk — and the bold claims from both sides.
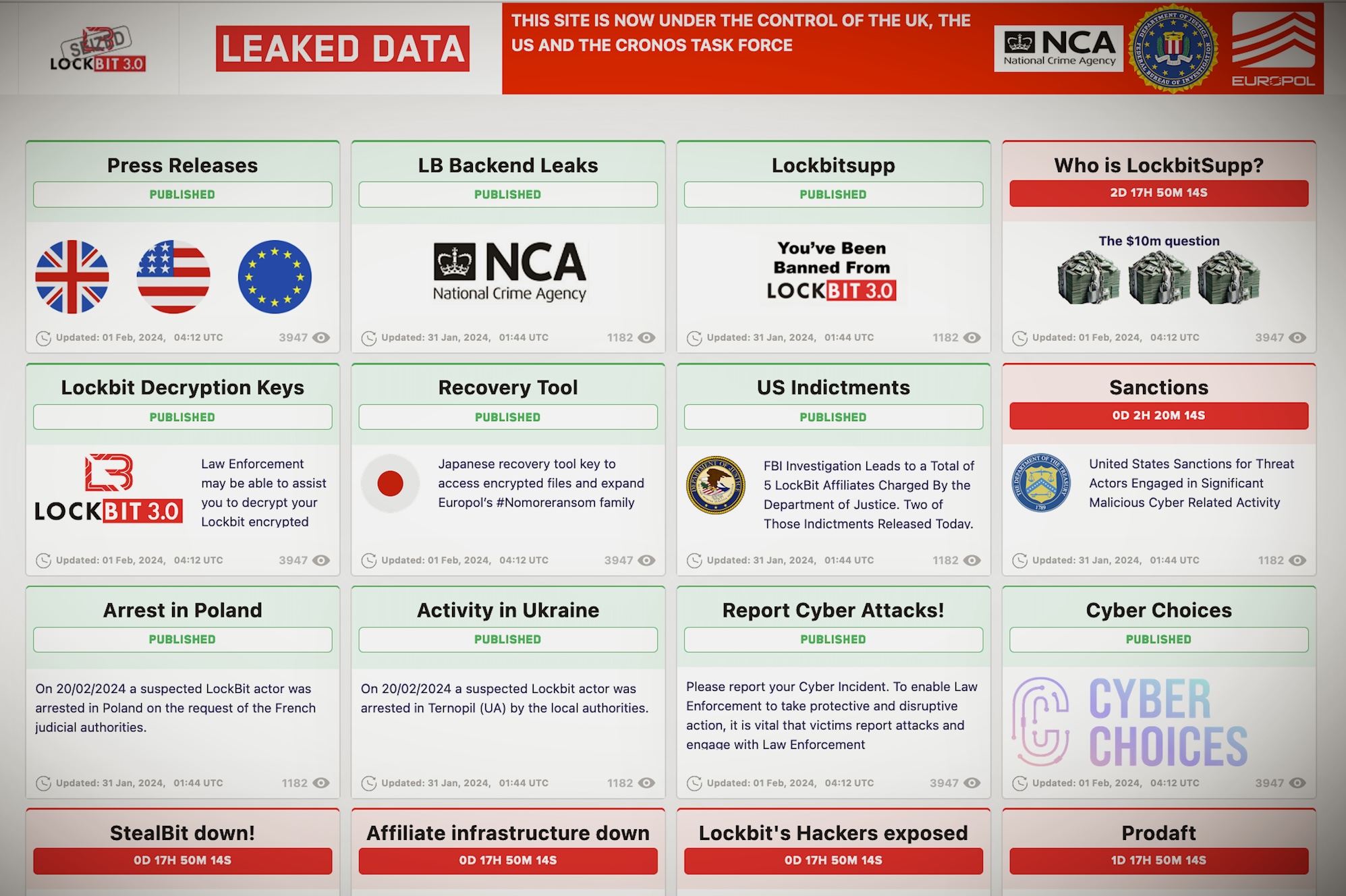
While the NCA promised a big reveal of the gang’s long-standing leader, who goes by the name of “LockBitSupp,” the agency disclosed little about the administrator in a post to LockBit’s own compromised dark web leak site on Friday.
“We know who he is. We know where he lives. We know how much he is worth. LockBitSupp has engaged with Law Enforcement :),” the vaguely worded NCA message read.
U.S. law enforcement agencies have also offered a multimillion-dollar reward for details “leading to the identification or location of any individual(s) who hold a key leadership position” in the LockBit gang — suggesting the authorities either don’t have that information or cannot yet prove it.
With the apparent administrator LockBitSupp still in action — the last remaining piece of the LockBit puzzle — it’s unlikely LockBit is going away. Ransomware gangs are known to quickly regroup and rebrand even after law enforcement disruption claims to have taken them down for good.
Take another Russia-based ransomware gang: ALPHV, also known as BlackCat, last year was dealt a similar blow when law enforcement agencies seized its dark web leak site and released decryption keys so victims could regain access to stolen files. Just days later, the ALPHV announced it “unseized” its leak site and claimed the FBI only had decryption keys for 400 or so companies — leaving more than 3,000 victims whose data remains encrypted.
At the time of writing, ALPHV’s leak site remains up and running — and continues to add new victims almost daily.
Other ransomware gangs, such as Hive and Conti, have faced similar law enforcement action in recent years but are said to have simply rebranded and re-formed under different names. Members of Conti are said to be operating under the new Black Basta, BlackByte, and Karakurt groups, while former Hive members rebranded as a new ransomware operation dubbed Hunters International.
The LockBit takedown, while hailed by many as one of the most significant in recent years, is unlikely to be much different — and the signs are already there.
In its long-winded post, LockBit claimed that law enforcement only obtained a handful of decryptors, arrested the wrong people, and failed to take down all of the websites under its control. LockBit also vowed that in light of the operation, it would upgrade the security of its infrastructure, manually release decryptors, and continue its affiliate program.
“No FBI with their assistants can scare me and stop me, the stability of the service is guaranteed by years of continuous work,” LockBit’s rant continued. “They want to scare me because they cannot find and eliminate me, I cannot be stopped.”
The NCA told TechCrunch that the agency “recognized LockBit would likely attempt to regroup and rebuild their systems” but acknowledged that the agency’s work continues to disrupt the group.
“We have gathered a huge amount of intelligence about them and those associated with them, and our work to target and disrupt them continues,” said NCA spokesperson Richard Crowe.
Law enforcement’s acknowledgment that it’s still working to disrupt the gang tells us all we need to know: LockBit isn’t dead yet, and it likely never was.
Why are ransomware gangs making so much money?